Control Network Newsletter

Addressing IP Security Concerns when Deploying a BACnet System
Previously published in BACnet Europe
BACnet is now the de-facto standard for building automation and management. It is an open protocol, works across devices from multiple vendors and its popularity will only further increase with time because of these factors. As with any protocol that becomes popular, "Security by Obscurity" approach is not a valid approach. Almost everyone has heard about HTTPS or Secure HTTP. This security is ensured with the use of IP security protocol called Transport Layer Security (TLS). 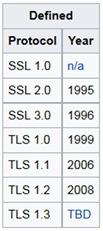 TLS is an industry standard being used for securing millions of HTTP transactions over the internet. Currently, TLS version 1.2 is in use. Its predecessor was Secure Sockets Layer (SSL). SSL version 1.0 (SSLv1) was developed by Netscape but was never publicly released. Version 2.0 and 3.0 were developed in the mid-1990s and used until a few years ago. SSL version 3.0 was the basis for TLS version 1.0 but SSL and TLS were not interoperable. As security flaws were discovered in SSL, the use of SSLv2 and SSLv3 was deprecated. TLS version 1.0 and 1.1 also suffered the same fate and only TLS version 1.2 is the recommended version that should be used to provide security. Even though, SSL is no longer in use and has been replaced by TLS, the term "SSL" continues to be used to refer to TLS. BACnet has its own Network Security definition which allows standard BACnet messages to become secure. BACnet Web services, BACnet/WS, can implement TLS and OAuth to provide security. OAuth (Open Authorization) is an open protocol that allows secure authentication and authorization. This is used to grant access to data for authorized applications. BACnet/WS which can utilize HTTPS and TLS is a more industry standard way of communicating in a secure manner. But not all BACnet devices support BACnet/WS. Furthermore, there are many devices where it is not possible to implement TLS or BACnet/WS. It is also not feasible to update all the legacy systems and applications in use to add security without incurring a high cost. Other options need to be used in such cases to fulfill the security needs when utilizing BACnet.
TLS is an industry standard being used for securing millions of HTTP transactions over the internet. Currently, TLS version 1.2 is in use. Its predecessor was Secure Sockets Layer (SSL). SSL version 1.0 (SSLv1) was developed by Netscape but was never publicly released. Version 2.0 and 3.0 were developed in the mid-1990s and used until a few years ago. SSL version 3.0 was the basis for TLS version 1.0 but SSL and TLS were not interoperable. As security flaws were discovered in SSL, the use of SSLv2 and SSLv3 was deprecated. TLS version 1.0 and 1.1 also suffered the same fate and only TLS version 1.2 is the recommended version that should be used to provide security. Even though, SSL is no longer in use and has been replaced by TLS, the term "SSL" continues to be used to refer to TLS. BACnet has its own Network Security definition which allows standard BACnet messages to become secure. BACnet Web services, BACnet/WS, can implement TLS and OAuth to provide security. OAuth (Open Authorization) is an open protocol that allows secure authentication and authorization. This is used to grant access to data for authorized applications. BACnet/WS which can utilize HTTPS and TLS is a more industry standard way of communicating in a secure manner. But not all BACnet devices support BACnet/WS. Furthermore, there are many devices where it is not possible to implement TLS or BACnet/WS. It is also not feasible to update all the legacy systems and applications in use to add security without incurring a high cost. Other options need to be used in such cases to fulfill the security needs when utilizing BACnet.
TLS Security
TLS or Transport Layer Security is the widely-used protocol to safeguard the internet and its communication by providing encryption of data. TLS provides confidentiality with the use of encryption. The encrypted data can be freely transmitted over the open internet without the ability to decipher the original data from it by a third party. Encryption involves the use of keys where the sender encrypts the data using a key and the receiver decrypts the data using a key. If the same key is used by both parties, it is called Symmetric Encryption. If different keys are used for encryption and decryption, then it is called Asymmetric Encryption or Public Key Encryption. Data integrity is provided with the use of hashing algorithms that safeguard against data tampering or loss of data due to communication problems. Hashing is a similar concept like having checksums but the hash algorithms are more sophisticated where the change of any data will result in a different hash. Two different sets of data should never produce the same hash and if it is found to be the case, the use of that hashing algorithm is then discouraged. A larger hash calculated on the data sets will be different and is the reason why the hash lengths in use keep increasing. TLS also provides authentication by ensuring the identity of the devices with the use of digital certificates. The use of certificates ensures that only authorized devices can communicate with each other.
VPN as an Alternative Approach
 For devices that don't implement BACnet/WS or devices with minimal memory where it is not possible to implement BACnet/WS with TLS or BACnet Network Security, a separate device like an IP router implementing VPN can provide security. VPN or Virtual Private Networks involve creating a secure connection between devices/networks. This secure connection is generally called a VPN tunnel and provides a way to send encrypted data. VPNs also use the TLS protocol to implement security. The data encryption takes place at the edge and the end devices are not computationally burdened with the task of encrypting or decrypting traffic and are free to perform their BACnet functions. Also, the existing applications don't need to change to add BACnet/WS to provide security. The BACnet device on one end sends the traffic where it is encrypted by one IP router and the encrypted data is then sent over the VPN tunnel to the IP router on the other end. The second router receives the encrypted data, decrypts it and the normal BACnet data is forwarded to the recipient BACnet device. Any type of data can be sent over the VPN and that includes BACnet/IP traffic. All the BACnet traffic utilizing any of the standard UDP ports, 0xBAC0 to 0xBACF, can be easily sent over this VPN tunnel and there is no need to make changes to the firewall configuration to accommodate the various BACnet UDP ports. The only port that needs to be configured in the firewall is the VPN port. VPN also has the added advantage that the end devices and the infrastructure behind the IP router providing VPN are hidden. It can be used to securely connect and monitor remote sites and program BACnet controllers. BACnet/MSTP devices can be used in conjunction with a BACnet/MSTP to BACnet/IP router and can also be communicated to securely over the VPN. VPNs are flexible and can be used to connect two sites or multiple sites securely. This is useful if it is a large campus and multiple buildings need to be connected. VPNs also provide the ability to configure access to different sites.
For devices that don't implement BACnet/WS or devices with minimal memory where it is not possible to implement BACnet/WS with TLS or BACnet Network Security, a separate device like an IP router implementing VPN can provide security. VPN or Virtual Private Networks involve creating a secure connection between devices/networks. This secure connection is generally called a VPN tunnel and provides a way to send encrypted data. VPNs also use the TLS protocol to implement security. The data encryption takes place at the edge and the end devices are not computationally burdened with the task of encrypting or decrypting traffic and are free to perform their BACnet functions. Also, the existing applications don't need to change to add BACnet/WS to provide security. The BACnet device on one end sends the traffic where it is encrypted by one IP router and the encrypted data is then sent over the VPN tunnel to the IP router on the other end. The second router receives the encrypted data, decrypts it and the normal BACnet data is forwarded to the recipient BACnet device. Any type of data can be sent over the VPN and that includes BACnet/IP traffic. All the BACnet traffic utilizing any of the standard UDP ports, 0xBAC0 to 0xBACF, can be easily sent over this VPN tunnel and there is no need to make changes to the firewall configuration to accommodate the various BACnet UDP ports. The only port that needs to be configured in the firewall is the VPN port. VPN also has the added advantage that the end devices and the infrastructure behind the IP router providing VPN are hidden. It can be used to securely connect and monitor remote sites and program BACnet controllers. BACnet/MSTP devices can be used in conjunction with a BACnet/MSTP to BACnet/IP router and can also be communicated to securely over the VPN. VPNs are flexible and can be used to connect two sites or multiple sites securely. This is useful if it is a large campus and multiple buildings need to be connected. VPNs also provide the ability to configure access to different sites.
Security is a moving target and what is safe and secure today may not be so tomorrow. Encryption relies on the ability for the encrypted data to be hard to crack and as computational power becomes cheaper, it is imperative that the devices providing encryption have the ability to easily implement the changes and enhancements to the TLS standard. Leveraging existing knowledge in the IT world and implementing some of their techniques to improve security is a step in the right direction.
Learn more about our IP Routers and the BAScontrol Series.